Secure video hosting protects business assets, internal training, and premium content by combining hosting with strong security practices. It prevents leaks of paid or gated content, keeps confidential materials safe, and ensures compliance with standards like GDPR and ISO. From onboarding videos to monetised media, choosing a secure hosting provider builds trust while meeting regulatory requirements. This article explains the essential features of video hosting security and how to assess providers.
Why is video hosting security important?
Choosing a secure video hosting platform reduces many business continuity risks by encrypting files, controlling access, and keeping sensitive business content safe. Unsecured video hosting leaves your content and your company exposed. Without the right protection in place, you risk data breaches, unauthorised access, or even pirated content circulating outside of your control. For businesses that rely on video for internal training, gated client content, or monetised assets, those risks can be costly. Sensitive material could be leaked. Paid content might be downloaded and shared freely. And if your videos include personal data or fall under regulated use cases, a security issue could mean serious privacy or compliance violations under frameworks like GDPR or ISO/IEC 27001.
Security in video hosting is also essential for protecting intellectual property, safeguarding your reputation, and ensuring only the right people see your content. It helps you stay in control, maintain compliance, and earn audience trust.

7 security features to look for in a video hosting platform
Not all video hosting platforms take security seriously. For this reason, you’ll need to keep an eye out for a number of must-have features that help keep your content protected. The list below will take you through some of the most important security features your video hosting platform should include.
1. Password protection and viewer authentication
Password protection is one of the simplest and most effective ways to control who can access your videos. From sharing internal training to hosting a client walkthrough or a gated webinar, this feature ensures only authorised viewers get through the door. Viewer authentication adds another layer by verifying individual users before granting access.
Secure video hosting platforms often allow you to create login requirements or unique access credentials for each viewer. This is especially useful when sharing confidential or paid content, or when complying with client NDAs and internal policies.
By locking access behind user authentication, you reduce the risk of content leaks and prevent competitors or uninvited users from viewing proprietary material. This level of controlled access is also valuable for nonprofits, community organisations, and churches that share member-only videos or sensitive internal content.
2. Domain and IP restriction
Domain and IP restriction features allow you to limit where your videos can be embedded or accessed; helping you control geography and context. Domain whitelisting ensures that your video can only appear on the specific websites that you authorise, which is vital when protecting premium content from being shared elsewhere.
IP restriction goes a step further by letting you block or allow video access based on geographic location or IP range. This is useful for enforcing regional licensing rights, protecting internal resources from public exposure, or restricting training access to specific office locations.
By tightening these controls, you safeguard your content from unauthorised distribution and keep it aligned with your intended use case.
3. Encryption in transit and at rest
Encryption is fundamental to secure video hosting, protecting your content from interception and unauthorised access. Strong platforms apply encryption at two critical stages:
- Encryption in transit: Uses HTTPS and TLS protocols to secure video data as it travels from server to viewer, preventing snooping or man-in-the-middle attacks.
- Encryption at rest: Stores your videos in an encrypted format on the server, making them unreadable without proper authorisation, even in the event of a backend breach.
These layers of protection are especially important for sensitive training videos, internal communications, and client-only deliverables. Together, they help mitigate a wide range of risks and support compliance with global standards like GDPR and ISO/IEC 27001.
4. Expiring links and time-based access controls
Time-based access controls let you set strict viewing windows for your videos. Expiring links, for example, ensure a video can only be accessed for a limited period of time, which is ideal for short-term campaigns, limited-time offers, or temporary client previews.
This prevents videos from being shared beyond their intended audience or used after their relevance has passed. Once the time limit is up, the link becomes invalid, protecting your content from unintended redistribution or piracy.
Secure video hosting platforms let you customise these settings per video, giving you better control over how long your content remains live and accessible without having to manually take it down.
5. Role-based access and user permissions
Especially in larger organisations, not everyone needs the same level of access. Role-based access controls allow you to assign specific permissions to users based on their responsibilities. For instance, a marketing team member might be able to upload and edit content, while a regional trainer can only view assigned videos.
This is particularly useful for maintaining workflow integrity and reducing the risk of accidental edits, deletions, or unauthorised sharing. By clearly separating who can do what, you keep sensitive content secure while allowing teams to collaborate more efficiently within the platform.
It’s a simple way to improve video hosting security without adding unnecessary friction to your operations.
6. Video watermarking and anti-piracy measures
Watermarking is a proactive deterrent against video piracy. Visible watermarks, such as a logo or user ID, signal that content is protected and discourage unauthorised distribution. Invisible watermarking, on the other hand, embeds unique identifiers into the video file itself, allowing you to trace leaks back to the source.
These tools are particularly important for monetised video content, confidential training, or pre-release materials. If a copy is leaked, invisible watermarks help you identify who shared it, while visible ones serve as a visual reminder that the content is protected.
Many secure video hosting providers offer built-in watermarking options for an added layer of defence.
7. Audit trails and analytics for suspicious behaviour
Detection is an important part of security in any field. And, when it comes to video hosting, audit trails and access analytics allow you to track exactly who watched what, when, and from where. This data is essential for identifying unusual patterns, such as repeated logins from multiple locations or excessive sharing of access credentials.
For regulated industries such as government agencies, law firms, and financial institutions, audit logs can also support compliance with policies like GDPR, HIPAA, or internal governance standards. They help you prove that content was only accessed by authorised individuals and flag potential breaches before they escalate.
By monitoring viewer behaviour in real time, you stay in control of your video content; even after it has been published.
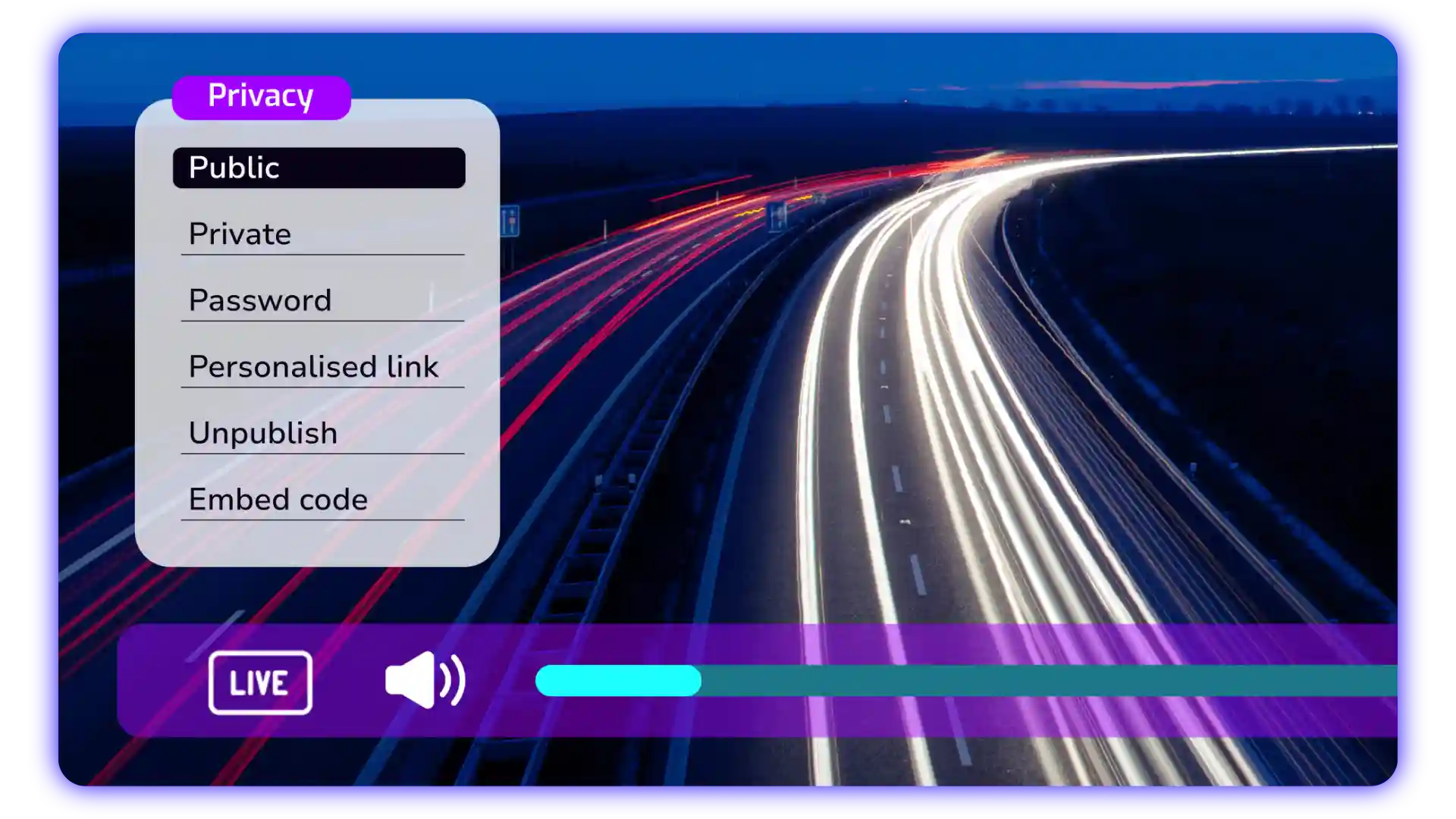
Is your video hosting platform secure enough?
If you’re using a video hosting platform today, it’s worth asking some security-focused questions. Some of these include:
- Does your video hosting platform provide the level of protection your business requires?
- Can you restrict access by IP address or domain?
- Do you have visibility into who’s watching your content, and from where?
- Are your internal or monetised videos staying private, or are they being shared externally without your knowledge?
Many popular hosting platforms prioritise reach and discoverability but lack advanced security tools. That may work for public content, but for training videos, client communications, or paid assets, it simply isn’t enough.
The good news? Secure video hosting doesn’t have to mean complicated setup or technical overhead. With the right platform and the proper streaming measures, you can maintain full control over your content while still offering a smooth, engaging viewing experience.
How Cinema8 helps you host videos securely
Cinema8 was designed with security at its core, helping you protect your video content without sacrificing usability. Whether you need to gate internal training, control who sees a product demo, or comply with global security standards, Cinema8 gives you the tools to do it all.
You can set passwords, restrict videos by domain or IP, and control access by user role. Share content through expiring links or place interactive elements behind permissions to ensure only the right people engage. With audit trails and viewer-level analytics, you’ll always know who’s watching and from where they’re watching.
As an all-in-one platform, Cinema8 lets you host, manage, and secure video content in one place.
Final thoughts on ensuring your video hosting is secure
In 2025, secure video hosting ensures that you can protect intellectual property, sensitive training materials, monetised content, and client trust. As video becomes more central to how businesses communicate and operate, ensuring your hosting platform is equipped with the right safety tools is no longer optional.
Security should be seen as a strategic priority. The cost of a breach (whether in revenue, reputation, or compliance) can far outweigh the investment in proper protection.
If you’re rethinking how your video content is managed and secured, it’s worth exploring a platform that puts protection front and centre. Cinema8’s secure video hosting combines enterprise-grade security with intuitive tools to help you share confidently and stay in control. Visit our website to learn how we can support your goals or choose a plan to start hosting your content right away.
